You might be interested in









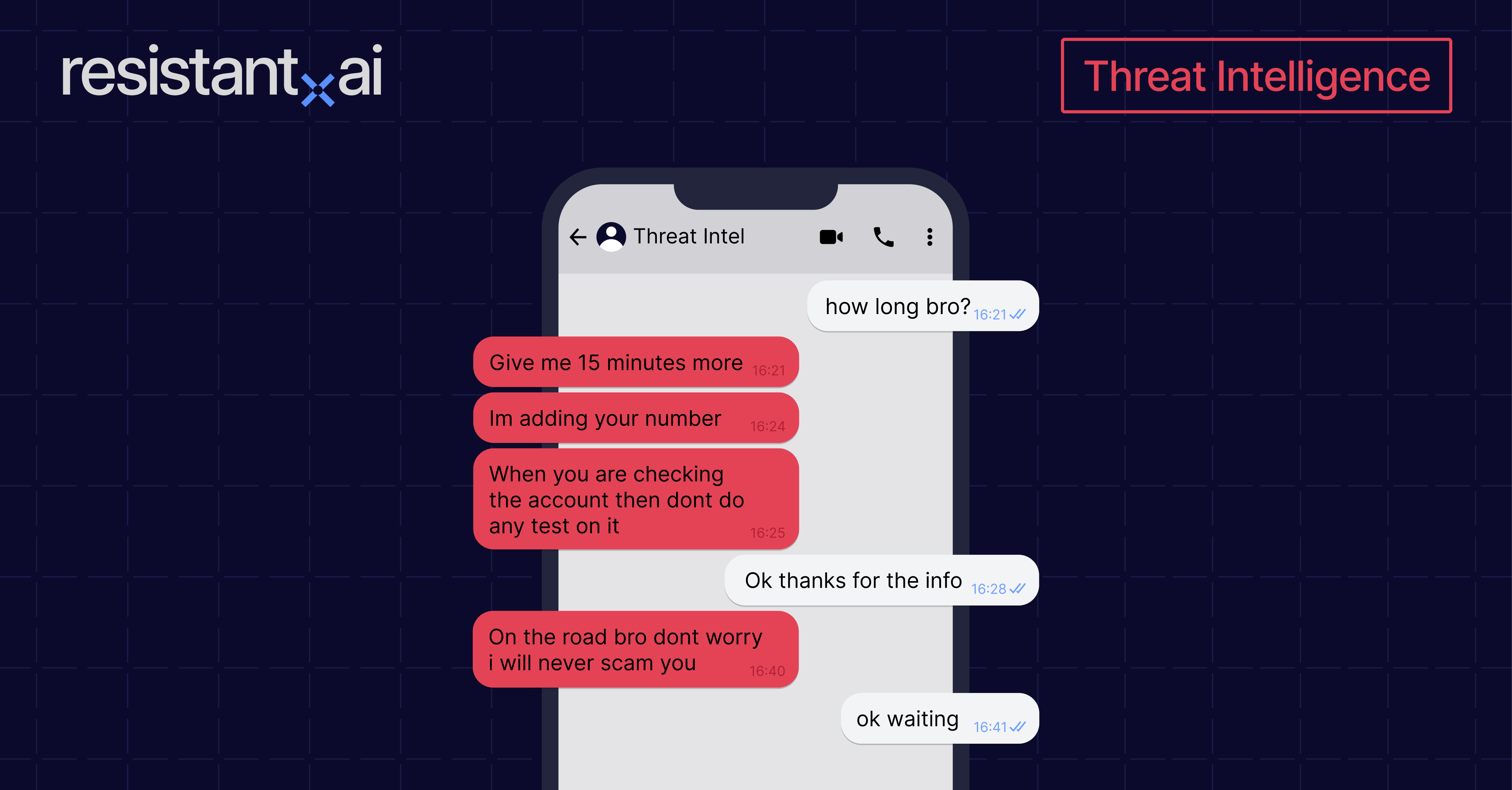
Talking to criminals can feel like you’re watching a foreign film with imperfect subtitles: the delivery is off, the motivations are suspect, and you’re never quite sure where the story is actually going.
That being said, a bad subtitle never stopped a film buff from watching Les Enfants du paradis, and an unusual Telegram channel never stopped a threat intel expert from learning more about fraud.
There’s a lot to extract from messaging and engaging with global fraud enablers. It provides a window into the minds of bad actors and the systems where they operate. If we can learn how they think and communicate, we’re one step closer to solving the puzzle (and stopping the crimes).
Here are my top 7 quotes from my conversations with template and account farmers, along with insights into why they’re so valuable.
Honor among thieves still exists in 2026.
Buying a fake document template or a verified account doesn’t come with any regulation or consumer protection rules. It’s all negotiation and trust in anonymous, digital personas. This makes a criminal’s honesty somewhat surprising in an environment where the buyer can (somewhat) easily be taken advantage of.
We have already experienced both scenarios. We’ve put trust into a farmer without them delivering or getting what we paid for. And we have also repeatedly witnessed farmers coming through on their promises and delivering the goods.
So far, template and account farmers have been delivering on their offering much more often than trying to cheat us.
The account farmer we talked to above is a perfect example of this. He did not scam us and the fake “verified” account he provided was real and active.
This also points to a harsh reality: fraud enablers want repeat customers, ones that will perceive the farmer as a trusted seller they can come back to, ideally frequently. Scammers clearly do and will exist within these criminal markets, but they’re not the norm.
The farmers that can deliver and do so are the threat here…better farmer practices result in more customers, which results in more fraud.
Solution engineering has become an increasingly indispensable part of the fraud enabler ecosystem.
We’ve now engaged with farmers who have entire workflows and technical support for their operations. They won’t just sell you a fake document or account. They’ll walk you through the entire process, setting everything up step by step.
They’ll even warn you of potential risks and recommend behaviors to minimize them.
Such a high level of customer care demonstrates farmers’ expertise and dedication to their clients, driving repeated purchases and the word-of-mouth spread of good reputation.
But maybe even more importantly, farmers do this to ensure their customers do not bring unnecessary attention to the fake templates or accounts they monetize.
This has serious implications both for fraud detection and prevention.
If the most sophisticated fraud enablers have technical experts and entire walkthroughs, you can bet they pay the same attention to the “products” themselves (i.e. accounts or documents), making sure they resemble the real thing as much as possible. We’ve already encountered offerings that are very hard (but never impossible) to detect properly.
We already know farmers are unkillable. But these kinds of interactions add further context to the level of sophistication some of them have attained and how they maintain that quality on both the buyer and seller sides of the equation.
In short, simple defense mechanisms won’t be enough, and only true, holistic financial crime prevention (aka defense-in-depth) can stay ahead of these adversaries.
How can the account owner not have access to his/her/their own account?
Farmers use multiple different tactics to onboard fake personal or business accounts.
One of those tactics we now think is happening frequently involves using real identities (whether sold, stolen or leaked) for account creation and onboarding.
This seems to have been the case here: we were negotiating the purchase of a business account for a payment platform and inquired about changing of credentials, when the account farmer essentially told us that the person whose identity is tied to the account does not hold credentials to it.
In fact, he/she/they likely don’t have any knowledge that the account exists.
This proves that many of the “verified” accounts sold in this fashion are likely opened without the individual’s knowledge.
In the words of good ol’ Dwight Schrute. “Identity theft is not a joke, Jim.”
And it is definitely not a joke. Can you imagine the police knocking on your own door? Being accused of money laundering activity conducted with an account in your own name you didn’t even know existed? This is happening right now. Possibly, at scales we can’t fully grasp…yet.
Even more threatening, on paper, these accounts look totally legit at creation and onboarding. Real people, real companies – simple registry checks or ID verifications won’t cut the cake here. To truly differentiate fake accounts from legit ones, you need to go deeper.
This also directly relates to something else we’ve seen happening (and will comment on below): batch-selling and monetization of leaked, stolen or sold identities.
The standard “verified” account package includes documents used for onboarding of the account. Any account purchaser may be asked to provide these documents for additional reviews or other actions during onboarding or throughout account ownership. After all, any real account holder would keep all the information tied to the account identity on hand.
In this particular case, we weren’t provided a utility bill that was supposed to be a part of the account package. We raised this issue with the account farmer. However, the criminal brazenly assured us they (i.e. the platform where the account was formed) “will not ask” (for a PoA document a second time).
Are these farmers overly confident? Or do they understand the document collection and verification processes of these platforms better than one might assume?
Once an account is “verified” and activated, farmers don’t seem to expect any additional documentation reviews. Platforms should keep this in mind. Repeated reviews of dormant or otherwise suspicious accounts might reveal a weak spot for the criminals involved.
For us, the seller was pretty confident we wouldn’t be asked, and if we were to be, he would simply “provide us from somewhere.”
This adds another contextual layer on top. Does the farmer even have the original utility bills used for onboarding?
Or could this utility bill be a part of some high-quality document set the farmer is using for onboarding but does not want to distribute further
Could giving everyone unlimited access to the same utility bill be a chink in the armor he couldn’t afford?
Is there any part of the farmer that would fear more competition appearing using the same fake documents to onboard accounts?
Or maybe he was trying to partially scam us all along, providing an active account but giving us a fake documentation package.
Either way, this exchange points to account farmers’ confidence (and perhaps reliance) that one-time document reviews are an industry standard.
Account farmers often offer accounts for numerous platforms across countries or segments (banks & payments, marketplaces, exchanges, crypto platforms, and so on).
To give some perspective, we’ve seen farmers with close to 2k offerings posted on Telegram within just 1 month. Some farmers offer accounts for almost 150 different companies, demonstrating the range, diversity, and scale of these offerings and the farming activity.
As opposed to industries or locales, farmers probably specialize in financial crime use cases. Instead of a “bank account expert,” they’re likely adept at cracking onboarding verification, not caring what platform or company the onboarding is connected to, as long as there’s some demand for it.
The speed of delivery and offers available only multiplies once you engage with the farmer and make your first purchase.
Suddenly, they can’t respond quickly enough. Your inbox will be flooded with additional offerings and requests to move forward. Just like any other customer success team, farmers try to upsell their clients often, and fast. And as we’ve said with quote no. 2 (above), farmers want repeat customers and long-term business relationships.
Why does this matter? It brings us back to serial fraud and the threat of multiple, repeated attacks orchestrated by fraudsters. Such criminal groups naturally have a wide demand for a variety of use cases and need to purchase large volumes of accounts at once.
Sellers are clearly ready to tackle this scale and only need a simple verification of intent to get started.
Rather than having multiple dormant accounts “in stock” on various platforms, farmers might be increasingly resorting to on-demand creation.
This makes tactical sense. Dormant accounts can be flagged or closed before they’re sold for a profit. We ourselves have made a point of looking at dormant accounts as potential suspects during the course of our account farming webinar last September.
Fraudsters will always iterate and learn themselves. Account farmers are not different. It’s very likely that some of them have had their dormant accounts closed, feeling the pain of investing time and resources to a product that was ultimately never sold.
Of course, turnaround time also factors into this market. Not having stock might put you at a competitive disadvantage. Fraudsters could want to work instantly, and sometimes the speed of acquiring a fake document or account might be crucial to their operation(s). After all, there are so many account farmers out there that you can very quickly find an alternative.
But this kind of behaviour on the side of the farmer points to a higher level of sophistication. Having the quality and professionalism to allow yourself to dictate the rules of engagement such as the turnaround time, even if it means losing some orders, could indicate a higher level of expertise and (consequentally) the threats at hand.
By protecting themselves and their offerings from the risks of dormancy, the account farmers are making it clear that they’re here to last indefinitely, not just taking people’s money and running for the hills. They want repeat customers. Which means repeat attacks, repeat strategies, and defenses that need to be repeatable and consistent as well.
During one of our conversations with a large-scale template farmer, he pointed us to a different channel that revealed a whole new threat vector.
Let’s call it “the identity market”, and it is also rapidly expanding.
We’ve seen subscription-based “identity market” channels offering huge numbers of various documents. Within these channels, all of the documents revolve around real identities, some even including “liveness” check assets (selfies or videos).
As in the case of documents in account selling, the purpose here might often be to provide a full “real identity package.”
But how did these channels acquire all of these real identities in the first place?
It should come as no surprise that one of the primary sources is large-scale data leaks, but these identities are also likely being sold by desperate individuals, or stolen (phished) within the context of various situations.
It’s also interesting to see the level of care farmers are taking with these real documents or visual assets. They’re only willing to distribute in closed, moderated environments with full visibility on activity and participation.
On the other hand, the price of entry into these environments is so low that you can get your hands on thousands of identities for less than 100 USD. Not a bad deal, right?
This is, of course, a huge problem, and one that has severe implications. If real identities and all the assets needed for onboarding (KYC or KYB) are that easy to come by, identity verifications alone cannot provide adequate defense.
Companies need to thoroughly inspect all documents requested (i.e. both ID and non-ID). They also need to evaluate any other contextual information available to minimize the risk of letting fraudsters into their systems.
Our perception of financial crime threat intelligence is not limited just to a few specific research vectors or operations.
And it’s definitely not just harvesting data on criminal markets, or trying to identify the next emerging threat via monitoring of these markets.
Embedding ourselves into these channels and conversations is equally important, if not even more. An illegal proof-of-concept if you will, demonstrating that these threats are being executed in the real world every day, not just as theories on a blog page.
As we’ve tried to demonstrate with the quotes above, actually talking to a fraud enabler might often yield insights or contextual information we would otherwise miss.
So you can be sure we’ll keep doing this, and our understanding of these threat actors will continue to grow. Check out our other Threat Intel articles if you’d like to learn more.
We definitely won’t scam you, bros.