Fraud detection: Ultimate guide


Fraud will forever be available and profitable. Just ask Chen Zhi, the baby-faced Cambodian tycoon who made nearly $30 million a day off forced labor and cryptocurrency scams.
Companies do their best, but keeping up costs a lot more than a line item on a balance sheet; it's a direct assault on a business's stability, its resources, and its relationship with customers. The only defense? Fraud detection: a must for any financial institution, fintech, or insurance provider heading into 2026.
The challenge, already very present in 2026, is that the tools used to commit this harm have become more powerful and accessible than ever before.
Generative AI can produce flawless fakes, mimic voices, and reproduce faces.
Online document fraud templates make it simple to create convincing pay stubs, business licenses, or any other document you can name.
Synthetic money mules purchase thousands of ready-to-use bank accounts from markets on Telegram.
A successful modern strategy requires a deep understanding of the various threats and the diverse technologies used to stop them.
This guide is designed to be that playbook. We will break down what fraud detection is, why it's so critical, the tools you need to do it right, and how to build a strategy that protects your business from the ground up.
What is fraud detection?
Fraud detection is the combination of processes and technology used to determine if a user, application, or financial action is legitimate or an attempt at deception.
The goal is simple: Protect the business and its customers from financial loss and reputational damage by spotting and stopping malicious activity before it's too late.
Why is fraud detection important?
The importance of fraud detection goes far beyond stopping a single bad transaction. Failing to manage it properly attacks a company's bottom line from three different angles: direct fraud losses, operational costs, and compliance.
- Direct fraud losses. This is the most straightforward cost: the money or goods that are literally stolen. It includes everything from chargebacks on fraudulent purchases to defaulted loans secured with fake documents.
- High operational costs. This is the price of fighting the war. It includes the salaries of ever-expanding manual review teams, the costs of them slowing down the overall process and creating more customer friction, and the licensing fees for the complex software they need to do their jobs.
- Compliance fines. This is the cost of failing to meet regulatory standards like anti-money laundering (AML) and know your customer (KYC) rules. These fines are not just a slap on the wrist; they can be existential threats.
“Fraud resilience makes trust between people possible; it’s one of the cornerstones of effective collaboration in human society. Even when we go back to ancient Mesopotamia, the cradle of civilization, people were still trying to scam each other.
Whether it's a faulty shipment of ancient copper, or an altered bank statement, humans have been attempting to thwart these crimes for millennia.
In response, many fundamental practices of trade and economy are examples of fraud resilience: accounting was designed to stop insider theft; verifiable invoices to end payment disputes; and signed contracts to provide non-repudiation. At their core, most business practices are structured to make fraud harder to conceal.”

How does fraud detection work?
At a high level, fraud detection works by looking for anomalies. It takes the repeatable, predictable, and standardized business processes we just mentioned to be able to recognize when something doesn't fit.
Every legitimate customer action, from opening an account, to the documents they submit, to how and when they make purchases, creates a set of data points.
Fraud detection systems are designed to constantly ingest and analyze these data points to find outliers, anomalies, and hidden patterns that signal a lie or suspicious behavior.
However, these anomalies can come in two forms: legitimate behavior and actual fraud. Identifying anomalies alone is relatively easy, when you have to distinguish fraud from the baseline AND legitimate behavior, that's when the trouble starts.
Real world example: Imagine finding the Nintendo Switch Lite or the latest Bose headphones you really wanted on a marketplace for an amazing price.
You go ahead, agree with the seller to transfer the money but the product never arrives. You've been defrauded by this scammer. But it could've been avoided if the right tech was in place.
Advanced fraud models look at the transaction in context and aim to minimize the false positives created by blanket rules applied by most transaction monitoring systems.
Did a transaction with a similar payment reference and the same counterparty happen before? Are there any identity features that connect the dots between seemingly unrelated parties? What are the odds that one legitimate entity has 10 Nintendo switches at home, ready for sale?
Advanced models will help your company block fraudulent transactions from as little as three transactions or even from its first attempt if the perpetrator decides to move to a new synthetic identity.
.png?width=1378&height=754&name=image%20(3).png)
And this is just one example of adept fraud detection at work. In general, the process can be broken down into three core steps: data collection, statistical analysis, and decision.
- Data collection. Where the system gathers all the relevant signals. For a document, this could be the digital structure of the file itself. For a transaction, it might be the user's IP address, the time of day, and the purchase amount.
- Statistical analysis. This is where the raw data is passed through a brain that looks for red flags. It involves applying mathematical models to the data to find deviations and outliers. This can be done online in real time (via an AI-powered solution), using the model to identify anomalies automatically. Or you can approach it yearly/retroactively, creating an offline rule-based statistical analysis based on already gathered data (for example, defining a specific value and flagging data that falls outside of it).
- Decision. Based on the analysis, the system makes a call. It can suggest to approve the action, deny it outright, or, if the signs are suspicious but not definitive, flag it for a human review.
While this explain the process at a rudimentary level, to truly understand fraud detection we need to divide it into the techniques that drive it, the data that feeds those techniques, and processes & platforms that make the decisions.
What are the techniques, data, and processes/platforms that make fraud detection possible?
Modern fraud detection is not powered by a single piece of magic software (or is it?) but by a layered ecosystem of techniques, data, and processes/platforms.
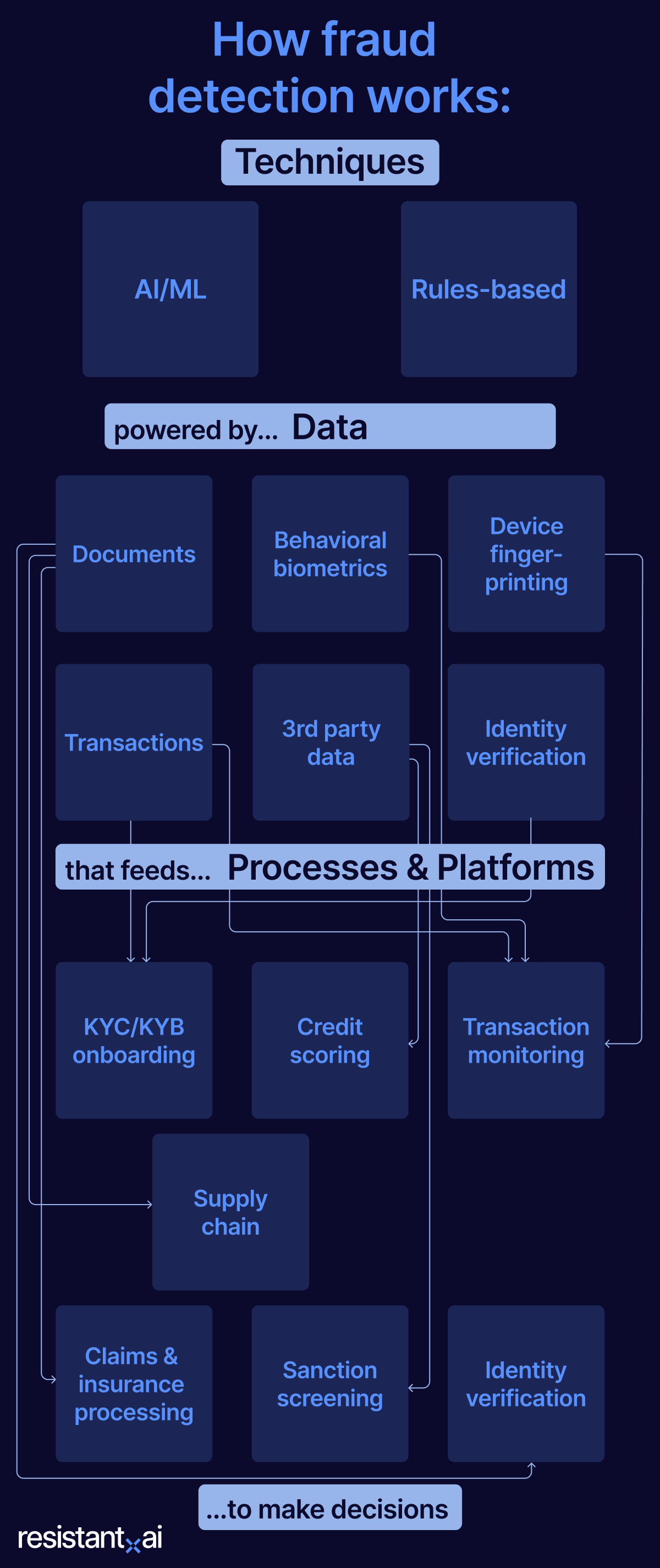
Fraud detection techniques
At the highest level, fraud detection techniques can be divided into two fundamental approaches: rules-based and AI/ML.
-
Rules-based. Uses a pre-defined set of "if-then" logic to make decisions. These rules are written and maintained manually by fraud analysts. For example: IF a transaction is >$10,000 AND originates from a high-risk country, THEN flag for review.
-
Artificial intelligence/Machine learning (AI/ML). Uses algorithms to learn the complex patterns of both legitimate and fraudulent activity from vast amounts of historical data. Instead of being told what to look for, the system discovers the subtle, hidden signals of fraud on its own.
The goal of both techniques is often the same: anomaly detection, or finding the exceptions that signal suspicious behavior. The critical difference lies in when and how they find them.
Rules-based anomaly detection is typically an "offline" process. Think of the forensic accounting practices used by the Big Four consulting firms.
They take a massive, static dataset (like a full year of company expense reports) and run a battery of rules against it to find non-compliant or suspicious entries. The analysis happens after the fact, providing a snapshot of past risk rather than preventing a present threat.
AI/ML-powered anomaly detection is an "online," real-time process. It analyzes events as they happen. The models create their own dynamic baseline of what "normal" looks like that is constantly updating and changing based on present data.
Then they flag any event that deviates significantly from that baseline in the moment. It doesn't analyze last quarter's data; it analyzes the transaction that is happening in the next 50 milliseconds, allowing it to stop fraud in motion before the damage is done.
But where do these techniques get the data that establishes that "normal" baseline?
What data feeds fraud detection?
Whether a system relies on human-written rules or adaptive AI, both techniques are useless without high-quality data. This data is the raw material used to build a baseline of trustworthy behavior: a predictable structure against which anomalies and outliers become visible.
The more diverse and reliable the data sources, the clearer the picture of a user's identity and intent (and the better the fraud detection).
Below are the most critical data sources that feed modern fraud detection systems.
Documents
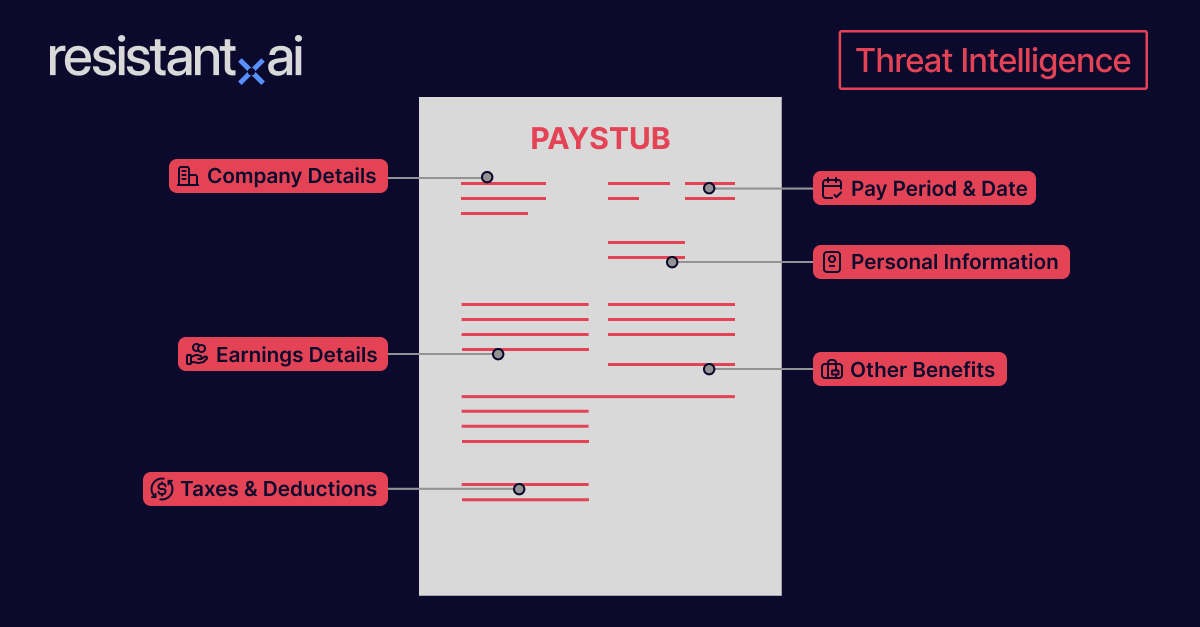
Documents are the primary evidence used in high-stakes decisions like onboarding, loan applications, and insurance claims.
By conducting forensic analysis of the documents, an AI model or rule-based technique can establish a baseline for what a 'pristine' document's digital DNA looks like.
A forgery, by its very nature, contains tell-tale anomalies that deviate from this baseline, allowing the system to instantly flag it as a high-risk fake.
Real world example: FIFA recently fined the football association of Malaysia for using forged documents to prove their player's citizenship.
Behavioral biometrics
A stream of data about how a user interacts with their device. This includes subconscious patterns like typing cadence, mouse movements, swipe gestures, and even the angle at which they hold their phone.
This data creates a unique physical signature for a digital user, which is nearly impossible for a fraudster to mimic, building a baseline of a user's normal physical interactions with their device.
In the news: Biometrics company BioCatch helped identify 150,000+ mule accounts in the APAC region in 2024.
Device fingerprinting
Hundreds of technical attributes about the device being used in a transaction, including its IP address, operating system, browser version, language settings, and screen resolution. This data is used to create a unique identifier for the device.
It provides critical context, like flagging suspicious activity, such as a user trying to hide their location with a VPN, a single device being used to open hundreds of new accounts, or the use of an emulator to impersonate a legitimate mobile device.
In the news: California colleges are using device fingerprinting to prevent financial aid fraud increasing their detection to over 90%.
Transactions
The ongoing stream of user actions, including payments, fund transfers, logins, and claims history.
This is the core data source for monitoring the ongoing customer relationship. Analyzing transactional behavior over time is essential for spotting patterns of money laundering, APP fraud, or uncharacteristic activity that signals a compromised account.
In the news: Transaction monitoring is financial institution's primary defense against APP fraud, like this recent case in India where a woman was coerced into transferring more than $600,000 to an attacker.
Third-Party Data
Authoritative information from external sources, such as government business registries, credit bureaus, international sanctions lists, and other public databases.
This data provides independent, third-party validation of the claims a user is making. It serves as a crucial cross-reference to confirm that a business is legitimate, a person's identity is not synthetic, and they are not a known bad actor.
In the news: UK Fintechs, telecoms, and technology companies have recently pledged to come together and share data in an effort to counter fraud and protect consumers.
Identity Verification
A collection of identity claims, such as name, date of birth, and address, often confirmed by comparing a government-issued ID document to a live selfie (liveness check).
In the news: Malaysia recently started investigating mandatory KYC identity verification on social media platforms to strengthen online safety.
While it provides critical data, identity verification is also a prime example of a process or platform. The act of capturing an ID, running a liveness check, extracting the data, and verifying it against third-party sources is a multi-step workflow.
This distinction highlights the final piece of the puzzle: the operational processes and platforms that bring these techniques and data together to make a final, automated decision on fraud.
What processes/platforms deliver fraud detection insights?
The data sources and detection techniques we've covered are the engine powering specific processes and platforms that are deeply integrated into a business's operations.
These platforms are designed to ingest the data, apply the techniques in real-time, and automate an initial judgment. They provide human experts with clear, actionable insights—like a risk score, a red flag, or a 'pass/fail' recommendation—allowing them to make faster, more accurate choices on which cases to approve, deny, or escalate within a fraud workflow.
Below are the most common platforms where this comes to life.
KYC/KYB onboarding
This is the process of verifying a new customer (Know Your Customer) or business (Know Your Business) when they first create an account. It is a regulatory requirement in many industries, designed to be the frontline defense that stops criminals, shell companies, and synthetic identities from ever entering your system.
A KYC/KYB platform is fed by documents, third-party data from government registries, and identity verification data.
It perform a forensic analysis of submitted documents like passports or certificates of incorporation, spotting forgeries. The platform delivers a clear recommendation ("Verified" or "Flagged for Forgery") allowing an onboarding specialist to confidently approve or deny an application.
Credit scoring
Credit scoring is the standardized process used by lenders to assess a consumer's creditworthiness. Its goal is to predict the likelihood that a person will repay a loan, condensing a complex financial history into a single, easy-to-understand numerical score that quantifies risk.
This process is powered almost entirely by third-party data sourced from the major credit bureaus, such as Experian, Equifax, and TransUnion, who compile an individual's history of payments, debt levels, and credit utilization.
This historical data is then fed into a highly regulated, rules-based statistical model (like FICO or VantageScore) to calculate the score. The platform delivers this score to a lender or underwriter as a critical, actionable insight that directly informs their decision on whether to approve a loan and at what interest rate.
Transaction monitoring
This focuses on the real-time analysis of a customer's financial activity after they have been successfully onboarded. Its purpose is to detect active criminal schemes as they unfold, such as money laundering, bust-out fraud, or payments related to scams.
Fed by a constant stream of transactions, device fingerprinting data, and behavioral biometrics, this platform uses AI/ML for real-time anomaly detection. It builds a baseline of normal behavior for each user and flags suspicious deviations.
A fraud analyst receives a prioritized alert (for instance, "this account is exhibiting behavior consistent with a mule account") giving them the actionable insight needed to investigate and freeze the account before more damage is done.
Claims & insurance processing
This process is used to validate the legitimacy of an insurance claim before a settlement is paid. It is designed to automatically filter out fraudulent or inflated claims, allowing insurers to process valid claims faster while protecting themselves from significant financial losses.
The primary data source is documents (medical reports, repair invoices, police reports, and other supporting evidence). Document forensics is used to find tell-tale signs of forgery, template usage, or digital alteration within these files.
The platform provides a claims adjuster with a clear signal ("this repair invoice is a forgery") allowing them to instantly deny the fraudulent claim and escalate the case to a special investigation unit.
Sanction screening
This is a legally required process where a platform automatically checks customers, vendors, and transaction counterparties against official lists of sanctioned individuals and entities. It is a non-negotiable part of compliance with Anti-Money Laundering (AML) and Counter-Terrorism Financing (CTF) regulations.
This is a rules-based process that is fed by constantly updated third-party data (the sanction lists). The platform's job is to automate the matching of names and identifiers against these lists with high precision. The output is a simple but critical insight for a compliance officer: a "Hit" or "No-Hit," which dictates whether the business can legally engage with that person or entity.
Supply chain security
This refers to platforms that secure a company's financial supply chain, specifically Accounts Payable (the money your company pays out to vendors) and Accounts Receivable (the money your company receives from customers). The goal is B2B fraud prevention, such as fake or duplicate invoices and payment diversion schemes.
These platforms ingest documents like invoices, purchase orders, bills of lading, etc, cross-referencing them with third-party data to verify vendor details.
They use a mix of rules-based checks (e.g., flagging a duplicate invoice number) and AI/ML to spot sophisticated forgeries.
An AP clerk receives an actionable alert like, "Warning: This invoice is from a known vendor, but the bank account details have been changed," preventing a fraudulent payment.
Identity Verification (IDV)
While IDV provides a crucial data feed, it is also a platform in its own right. As a process, it is designed to answer a single question: is this person real, and are they the legitimate owner of this identity document? It is the foundational step for many other fraud prevention workflows.
The IDV platform orchestrates a multi-step process. It uses a person's device to capture an image of their document (like a driver's license) and a live biometric marker (like a selfie).
It then uses AI to forensically analyze the document's authenticity, extract its data, and compare the photo on the ID to the live selfie. The platform's output is a foundational insight ("Identity Verified") that is then consumed by other systems like a KYC platform.
What are the most common types of fraud?
Now we understand how fraud detection works and the tools, processes, and data involved. But how can we use it to combat fraud? Fraud manifests in many ways, from simple scams to highly sophisticated criminal operations.
While each of the following types has nuances that could fill its own dedicated article, a foundational understanding of the threat landscape is the essential first step in building an effective defense.
As a document fraud detection and transaction monitoring company, we’ve connected each threat to the relevant solution, categorizing each type of fraud by the primary defense used to combat it: document fraud detection, transaction monitoring, or multi-layered.
- Document fraud. This is the act of creating, altering, or using a falsified document to deceive. It is often the critical first step that enables many other types of financial crime, like creating a fake identity to open an account or providing fake evidence to support a fraudulent claim. The eight types of document fraud include: document forgery, document alteration, identity theft/stolen documents, synthetic identities, template fraud, pre-digital modification, generated document fraud, and serial fraud.
- Defense: Document fraud detection. It works by forensically analyzing the structure of a file to find the hidden, digital proof of forgery.
- Defense: Document fraud detection. It works by forensically analyzing the structure of a file to find the hidden, digital proof of forgery.
- Synthetic identity fraud. A sophisticated fraud where criminals combine real information, like a stolen social security number, with fabricated details to create an entirely new, fictitious identity. This "synthetic" person is then used to open fraudulent accounts and apply for loans.
- Defense: Multi-layered. Document fraud detection is crucial for spotting fake proof-of-address or ID documents used to build the identity's legitimacy. Post-onboarding, transaction monitoring is key to spotting bust-out schemes. These defenses are often complemented by data verification services that check for anomalies, like a Social Security Number that has no credit history.
- Defense: Multi-layered. Document fraud detection is crucial for spotting fake proof-of-address or ID documents used to build the identity's legitimacy. Post-onboarding, transaction monitoring is key to spotting bust-out schemes. These defenses are often complemented by data verification services that check for anomalies, like a Social Security Number that has no credit history.
- Account takeover (ATO). A criminal gains unauthorized access to a legitimate user's online account, often using credentials stolen from a data breach to drain funds, steal personal information, or use the account to defraud others.
- Defense: Multi-layered. Transaction monitoring is the primary tool for flagging uncharacteristic behavior after a successful login, such as rapid transfers. However, it works in concert with other key technologies like behavioral biometrics and device fingerprinting to detect an imposter during the login itself. Document fraud detection prevents fraudsters from using fake IDs to socially engineer a help desk for a password reset.
- Defense: Multi-layered. Transaction monitoring is the primary tool for flagging uncharacteristic behavior after a successful login, such as rapid transfers. However, it works in concert with other key technologies like behavioral biometrics and device fingerprinting to detect an imposter during the login itself. Document fraud detection prevents fraudsters from using fake IDs to socially engineer a help desk for a password reset.
- Loan application fraud. An applicant intentionally provides false information to secure a loan or mortgage to inflate income, hide debt, or secure funds for a business that doesn't exist.
- Defense: Document fraud detection. This is the most critical defense. It automatically analyzes submitted documents like pay stubs, bank statements, and business licenses, working alongside traditional data sources like credit bureau reports.
- Defense: Document fraud detection. This is the most critical defense. It automatically analyzes submitted documents like pay stubs, bank statements, and business licenses, working alongside traditional data sources like credit bureau reports.
- Insurance claims fraud. This is the act of submitting falsified evidence to support a claim for a loss that never happened or was less severe than reported.
- Defense: Document fraud detection. This defense automatically verifies supporting evidence. It can spot a fake police report, a doctored medical invoice, or a fraudulent repair estimate. For uncovering more complex, organized fraud rings, insurers may also use network analysis to find hidden connections between claimants and providers.
- Defense: Document fraud detection. This defense automatically verifies supporting evidence. It can spot a fake police report, a doctored medical invoice, or a fraudulent repair estimate. For uncovering more complex, organized fraud rings, insurers may also use network analysis to find hidden connections between claimants and providers.
- Money laundering. This is the process of making illegally gained proceeds, or "dirty money," appear legal by funneling it through a series of legitimate-seeming transactions. The goal is to obscure the criminal origins of the funds.
- Defense: Transaction monitoring. This is the classic use case for transaction monitoring. It is designed to analyze complex patterns of financial behavior over time to spot the red flags that signal a money laundering scheme.
- Defense: Transaction monitoring. This is the classic use case for transaction monitoring. It is designed to analyze complex patterns of financial behavior over time to spot the red flags that signal a money laundering scheme.
- Insider fraud. This fraud is committed against a company by its own trusted employees, managers, or contractors. Common examples include embezzling funds, faking expense reports, or stealing sensitive customer data for personal gain.
- Defense: Multi-layered. Transaction monitoring can identify unusual internal financial activity, such as an employee transferring funds to an external account. Document fraud detection is needed to catch falsified evidence, like a doctored receipt submitted for an expense report.
- Defense: Multi-layered. Transaction monitoring can identify unusual internal financial activity, such as an employee transferring funds to an external account. Document fraud detection is needed to catch falsified evidence, like a doctored receipt submitted for an expense report.
- Chargeback fraud. A common type of payment fraud, this happens when a customer falsely claims a transaction was unauthorized or a product was never delivered to get their money back.
- Defense: Multi-layered. The key defense is analyzing behavioral data and historical patterns. This includes a customer's history of chargebacks, their device information, and their purchase history to distinguish between legitimate disputes and serial abuse. Transaction monitoring systems are designed to flag these high-risk behavioral patterns.
- Defense: Multi-layered. The key defense is analyzing behavioral data and historical patterns. This includes a customer's history of chargebacks, their device information, and their purchase history to distinguish between legitimate disputes and serial abuse. Transaction monitoring systems are designed to flag these high-risk behavioral patterns.
- Business email compromise. A criminal impersonates a company executive or a trusted vendor over email. They aim to trick an employee with access to finances into making a large wire transfer to a fraudulent account.
- Defense: Transaction monitoring. While email security is the first line of defense, transaction monitoring provides the critical final check. It can flag a payment to a new, unverified vendor account or a transfer that deviates from the company's normal payment patterns.
Fraud detection challenges (and how to solve them)
The modern fraud landscape is a difficult environment, but the same technologies that empower criminals can also provide the solutions. While other guides might simply list the problems, we’ve provided tips and strategies based on our experts.
Fraudsters keep reiterating
Fraudsters are constantly changing their tactics, techniques, and procedures. As soon as a defense is built for one type of scam, criminals have already moved on to the next, making it nearly impossible for static, rule based systems to keep up.
Solution: AI-powered software is designed to adapt. Through continuous learning and anomaly detection, these systems can identify new and emerging fraud patterns in real time, even if they have never seen that specific type of attack before.
“The fundamental property of fraud is that it never stops, it's never solved, and you never win. You can only make it less damaging and less likely to happen.
You can have perfect security in certain parts, but it's impossible to be perfectly secure. If you’re creative enough, have enough resources, you can always get around it.
If I buy a perfect, impenetrable lock for my door, all the criminals have to do is compromise the factory and the employees will deliver a copy of the key.”

Data privacy and compliance
To detect fraud, you need to analyze data, but regulations like GDPR and CCPA put strict limits on how personal information can be handled. This creates a difficult balancing act between having enough data to be effective and respecting customer privacy.
Solution: Some advanced AI software, particularly for documents, can analyze the structure of a file without ever processing the personally identifiable information on the page. This allows it to determine if a document is a forgery based on its digital forensics alone, completely bypassing privacy concerns.
Imperfect models
False positives happen when a legitimate customer or transaction is incorrectly flagged as fraudulent. This creates a terrible user experience, leading to customer churn and lost revenue, while also wasting the time of review teams who have to manually correct the system's mistakes.
Solution: Modern AI models are trained on massive, diverse datasets, allowing them to understand the subtle nuances of normal behavior far better than rigid rule based systems. This high level of accuracy means they can significantly reduce the number of false positives, letting good customers pass through without friction. Additionally, linking signals across transaction monitoring, document processing, and other defenses can help siloed systems learn from one another and further improve accuracy.
The availability of fraud templates
The internet is flooded with high quality, easily editable templates for almost any document imaginable, from passports to bills of lading. This allows criminals to quickly produce convincing fakes at a massive scale, rendering manual inspection unreliable.
Solution: AI document fraud software is specifically designed to defeat templates. It can identify the common signatures of a template, such as non-standard fonts, metadata from editing software, or signs that text has been digitally inserted into pre-existing fields.
Balancing security with customer friction
If your fraud prevention measures are too aggressive, you will inevitably block legitimate customers and create a frustrating experience. This friction can directly harm revenue and damage your brand's reputation more than the fraud itself.
Solution: AI allows for a dynamic approach tuned to your institution’s risk appetite. It can instantly filter genuine high risk events from benign anomalies, applying a light touch for good users and reserving high friction checks only for the most suspicious cases.
LLMs and Gen AI
Generative AI can create flawless fake documents, write convincing phishing emails, and even produce deepfake videos that can fool liveness checks. This technology makes high quality forgeries accessible to even low skilled fraudsters, overwhelming manual review teams and legacy systems.
Solution: The only effective way to fight AI is with AI. AI-powered detection software does not rely on spotting the visual errors that GenAI has eliminated. It performs a structural analysis of a file's digital makeup to find the hidden, tell-tale signs of AI generation that are invisible to the human eye.
“Most real world frauds are not movie-style heists, they are repetitive and scalable, exploiting basic human vulnerabilities (greed, desperation, need for human contact, social validation) without concern for who’s hurt or how many times you run the same scheme.
Now that’s made exponentially worse by digital communication, internet, and AI. That’s why the only defense is one that can change, evolve, and adapt to new threats as they emerge: because the criminals will never stop iterating.”

What business workflows require fraud detection?
Fraud detection is a critical layer of security that must be applied at various points in the customer lifecycle. The first step is knowing what workflows need to be protected:
- KYC and KYB onboarding: Verifying a new customer or business's identity before they are approved.
- Loan and mortgage applications: Assessing an applicant's creditworthiness for a loan by validating their financial documents.
- Insurance claims processing: Validating a claim by authenticating supporting evidence before paying out a settlement.
- Tenant and employee screening: Verifying applicants for a rental property or a job by checking their IDs and credentials.
- AML compliance: The legally required process of monitoring customer transactions to prevent financial crime.
- "Buy now, pay later" (BNPL) services: Providing instant, point-of-sale credit to consumers based on behavioral analysis.
- Authorized push payment (APP) fraud. Preventing scams where a customer is tricked into sending money from their own account to a fraudster.
- Ongoing account monitoring: The continuous observation of active user accounts for signs of a compromise or takeover.
Real world examples of fraud detection
To see how these concepts work in practice, it is helpful to look at how different companies have applied fraud detection technology to solve specific, high stakes problems.
Payoneer stops onboarding fraud at scale
A global payments platform like Payoneer needs to onboard millions of users, but manual reviews were a bottleneck while dealing with sophisticated document forgeries. By integrating an AI-powered solution, they were able to automate the analysis of documents at a massive scale. This allowed them to instantly block fraudulent applications while speeding up the document verification process for legitimate customers.
Finom enhances cross-border AML monitoring
As the European fintech Finom expanded into new countries, they needed a more advanced way to accurately identify suspicious behavior across different markets. By layering transaction monitoring on top of their existing rules-based system, they could move beyond rigid rules. This enhancement allowed them to significantly reduce false positives, enabling their compliance team to conduct faster and more effective investigations into the most critical alerts.
What are the legal requirements of fraud detection?
For many industries, particularly financial services, fraud detection is a legal and regulatory obligation. Depending on your institution’s location, the laws regarding the prevention, detection, and reporting of financial crime may differ.
Still, failure to comply with these rules can result in severe penalties, including massive fines and the loss of operating licenses, regardless of where you’re located.
Here are some of the most important legal and regulatory principles that govern fraud detection.
Anti-money laundering (AML) regulations.
A global framework of regulations designed to stop criminals from disguising illegally obtained funds as legitimate income.
- Relevant legislation: Bank Secrecy Act (USA), Proceeds of Crime Act 2002 (UK), The Anti-Money Laundering Directives (EU), Corruption, Drug Trafficking and Other Serious Crimes (Confiscation of Benefits) Act (Singapore), Anti-Money Laundering and Counter-Terrorism Financing Act 2006 (Australia), Proceeds of Crime (Money Laundering) and Terrorist Financing Act (Canada), Law No. 9.613/1998 (Brazil).
Know your customer (KYC)
Core principle of AML regulations, requires businesses to verify the identity of their clients to prevent anonymous or fraudulent accounts.
- Relevant legislation: Customer Identification Program (CIP) rules under the USA PATRIOT Act (USA), The Money Laundering, Terrorist Financing and Transfer of Funds Regulations 2017 (UK), The Anti-Money Laundering Directives (EU), MAS Notice 626 (Singapore), Anti-Money Laundering and Counter-Terrorism Financing Rules Instrument 2007 (Australia), Proceeds of Crime (Money Laundering) and Terrorist Financing Act and associated Regulations (Canada), BCB Circular No. 3,978/2020 (Brazil).
Sanctions screening
This is the legally required process of screening all customers and transactions against official lists of sanctioned individuals, entities, and countries. It is a strict liability requirement, meaning that violations can lead to penalties even if they were unintentional.
- Relevant legislation: International Emergency Economic Powers Act (IEEPA) which governs OFAC (USA), Sanctions and Anti-Money Laundering Act 2018 (UK), Common Foreign and Security Policy (EU), United Nations Act (Singapore), Autonomous Sanctions Act 2011 (Australia), Special Economic Measures Act (Canada), various regulations from the Central Bank of Brazil implementing UN sanctions (Brazil).
Data privacy and protection
This is the principle that any fraud detection system must handle customer data lawfully, transparently, and securely. It governs how personal information is collected, stored, and processed.
- Relevant legislation: State laws like the California Consumer Privacy Act (USA), UK GDPR and Data Protection Act 2018 (UK), General Data Protection Regulation (EU), Personal Data Protection Act (Singapore), The Privacy Act 1988 (Australia), Personal Information Protection and Electronic Documents Act (Canada), Lei Geral de Proteção de Dados (Brazil).
Fair credit reporting
This principle regulates how consumer information is used in decisions, particularly those made by automated systems. It often includes the right for a consumer to be notified of an "adverse action," such as being denied a loan, based on the data used.
- Relevant legislation: Fair Credit Reporting Act (USA), The Consumer Credit Act 1974 (UK), The General Data Protection Regulation: Article 22 (EU), The Credit Bureau Act (Singapore), The Privacy Act 1988: Part IIIA (Australia), various provincial Consumer Reporting Acts (Canada), The Consumer Defense Code (Brazil).
How to get started with fraud detection
If you’ve made it this far then you’re probably in the process of putting a modern fraud detection strategy in place.
It can seem daunting, but we’re here to break it down into a series of logical steps. Let’s get started.
- Conduct a comprehensive risk assessment. Start by mapping out your customer journeys, from onboarding to payment, and identify the specific points where you are most exposed to fraud. A risk assessment provides the blueprint for your entire strategy, ensuring you focus your resources where they are needed most.
- Establish clear internal policies and review processes. Create clear, documented policies for how to handle suspicious activity. Define what happens when an application is flagged, who is responsible for the manual review, and what the escalation path is for high-risk cases.
- Analyze your historical fraud data. Dig into your past fraud cases to identify the common patterns and techniques (in both transactions and documents use cases). This data will provide a critical baseline for understanding your specific threats and will be invaluable for configuring and training your detection systems.
- Adopt AI-powered fraud detection software. The final, critical step is to adopt AI-powered software that can automate the detection of these advanced threats in real time, allowing you to stop fraud at scale while providing a seamless experience for your legitimate customers.
What does fraud detection look like in 2026?
To understand what fraud detection will look like in the near future, we have to examine the new tools criminals are using, the expanding digital territories they are attacking, and the next generation of defenses required to stop them.
.png?width=1400&height=800&name=Fraud%20detection_%20New%20Weapons%2c%20Battlefields%2c%20and%20Defenses%20(2).png)
New fraud weapons
The tools used to commit fraud are more accessible and sophisticated than ever before. The rise of generative AI allows any fraudster to create documents and synthetic identities that are visually perfect and indistinguishable from the real thing.
This is compounded by a thriving underground economy that offers Fraud-as-a-Service, giving low-skilled criminals access to powerful tools for a small fee.
Tactics to look out for:
- Generative AI for document creation
- Synthetic identities
- AI-powered social engineering and vishing
- Deepfakes and video impersonation
- Fraud-as-a-Service (FaaS) platforms
- Verified account selling
- Automated bot attacks for account creation and testing
New fraud battlefields
As every aspect of commerce and finance becomes digital, the surface area for attack has grown exponentially. Fraud is no longer concentrated in a few specific areas. It is now a threat across the entire customer lifecycle and in every industry, from the instant it takes to get a "buy now, pay later" loan to the complex web of international trade finance.
New areas for attack:
- Digital onboarding (KYC/KYB)
- Trade finance and supply chain operations
- Insurance claims automation
- Instant lending and "Buy Now, Pay Later" (BNPL) platforms
- Loyalty programs and digital marketplaces
- Government benefit and stimulus programs
- Fintech and embedded finance ecosystems
New defenses
Legacy defenses and manual review processes are no match for AI-powered attacks. The only way to effectively combat these new weapons is to fight AI with AI. The next generation of defenses moves beyond simple data checks and instead uses machine learning to find the hidden, structural, and behavioral signals of fraud that criminals cannot hide.
Modern defenses:
- Structural document analysis
- Behavioral biometrics
- Advanced device fingerprinting
- Liveness detection and anti-spoofing tech
- Layered defenses and network-level analysis
- Real-time, AI-powered transaction monitoring
“The big difference is the scalability of fraud in digital environments.
You can’t go into the same bank as the same person and open 1000 accounts with 1000 different ID cards. But, if you do this with an API in a digital domain, no one notices.
It’s our job to notice and return common sense to decision makers. The same human who got scammed on copper all those centuries ago made their decision based on gut feelings and expertise. We want to return that level of confidence to our digital world.
At that time, clay tablets were seen as a source of truth. Now we trust silicon. Nothing fundamentally has changed except the writing surface.”

Conclusion
The central question is no longer if you need fraud detection, but how you can implement a strategy that is resilient enough to win in the modern environment. You must fight sophisticated, AI-powered attacks with a defense that is even smarter. The old way of reviewing documents and monitoring transactions is over.
Resistant AI was built to provide this next generation of defense. We offer a suite of solutions that protect the entire customer lifecycle, securing your business from the moment a user applies to every action they take thereafter.
Resistant Documents acts as your digital gatekeeper, using AI-powered forensic analysis to instantly spot fake and altered documents at onboarding or during high-stakes processes like loan applications.
Resistant Transactions is the guardian for your active users, using behavioral analysis to monitor accounts and stop fraud in motion before it can cause damage.
By combining these defenses, you can create a secure environment that locks out bad actors from the start and protects your trusted customers from within. This is how you move beyond simply reacting to fraud and start actively resisting it.
Scroll down to book a demo!
Frequently asked questions (FAQ)
Hungry for more fraud detection content? Here are some of the most frequently asked questions about fraud detection from around the web.
Is there software that can detect fraud?
Yes. Specialized AI-powered fraud detection software exists to detect fraud in both documents and financial transactions by analyzing them for signs of forgery or malicious behavior.
What are the basics of fraud detection?
The basics of fraud detection are:
- Collect data.
- Analyze it for anomalies and patterns that indicate deception.
- Make a decision to either approve, deny, or review the action.
What is an example of a fraud detection model?
A common example is an anomaly detection model. This is a type of machine learning model that learns what normal behavior looks like for a user and then flags any activity that significantly deviates from that established pattern.
How to detect fraud?
You detect fraud by using technology to find signals of deception. This involves analyzing the digital forensics of a document to prove it's a fake or monitoring user behavior to spot actions that suggest a criminal intent.
How to detect fraud in online transactions?
Fraud in online transactions is detected by using real-time monitoring software to analyze behavioral patterns, device information, and payment details. This system flags transactions that deviate from a user's normal activity or match known fraud signatures.
How to detect fraud in documents?
Fraud in documents is detected by using AI-powered software to perform a forensic analysis of the file itself. This process ignores the information on the page and instead finds the hidden digital evidence of forgery, editing, or template usage.