The missing link connecting all of your risk signals

Leverage the data you already generate across your entire tech stack for faster fraud detection, with more clarity and confidence.

The missing link connecting all of your risk signals
Leverage the data you already generate across your entire tech stack for faster fraud detection, with more clarity and confidence.
Crime has changed. Fraud and fincrime prevention need to
AI-generated documents, fake identities, and pre-verified bank accounts are sold daily on online marketplaces. Full-service fraud and money laundering networks help criminals exploit every gap in your risk and compliance processes. Break your fraud detection and AML teams out of their siloes and start proactively hunting the criminals down before they scale.
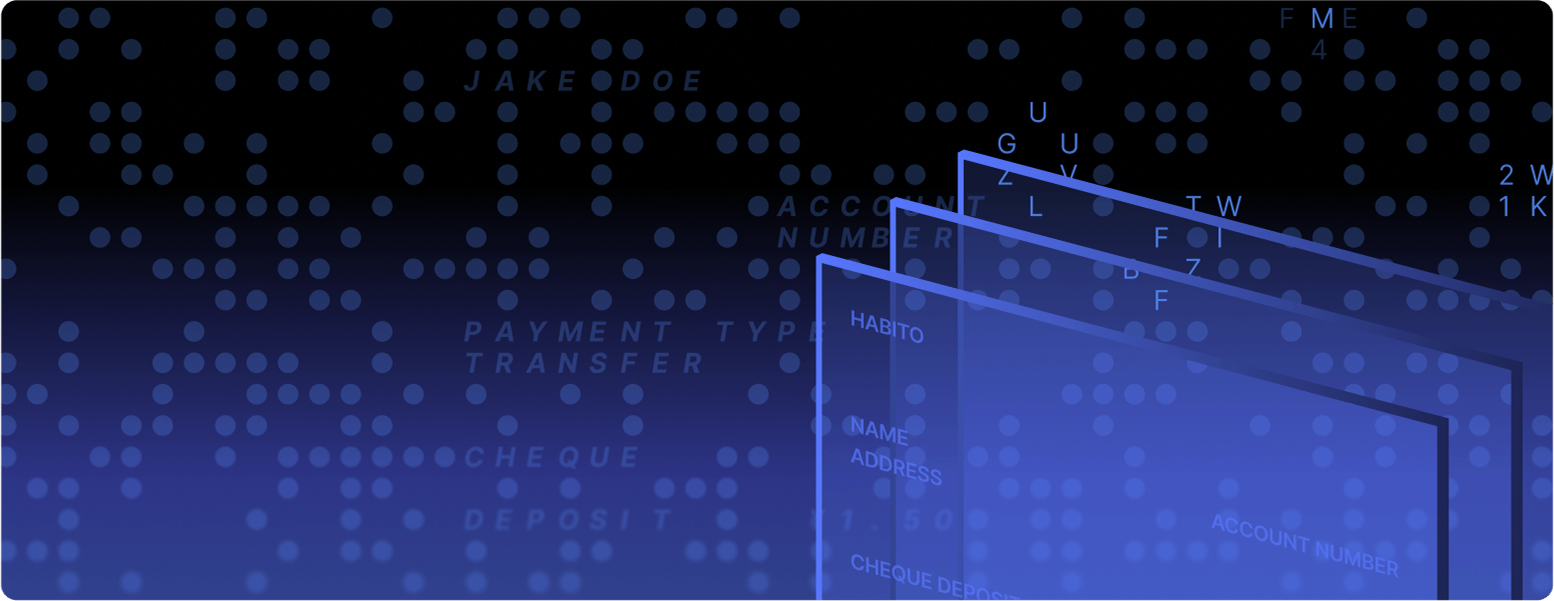
Get insights from Documents...
Whether submitted at onboarding, or as part of an EDD process, analyze any document and cross-reference against all others.
...Behaviors & devices...
Server timestamps, buttons clicked, keyboard strokes, IP addresses used, device IDs, screen resolutions... All these latent data points tell a story.
...Transactions...
Each account, transaction, counterparty, money flow, alert, and more is a signal that can be enriched with additional context.
...And any other data point.
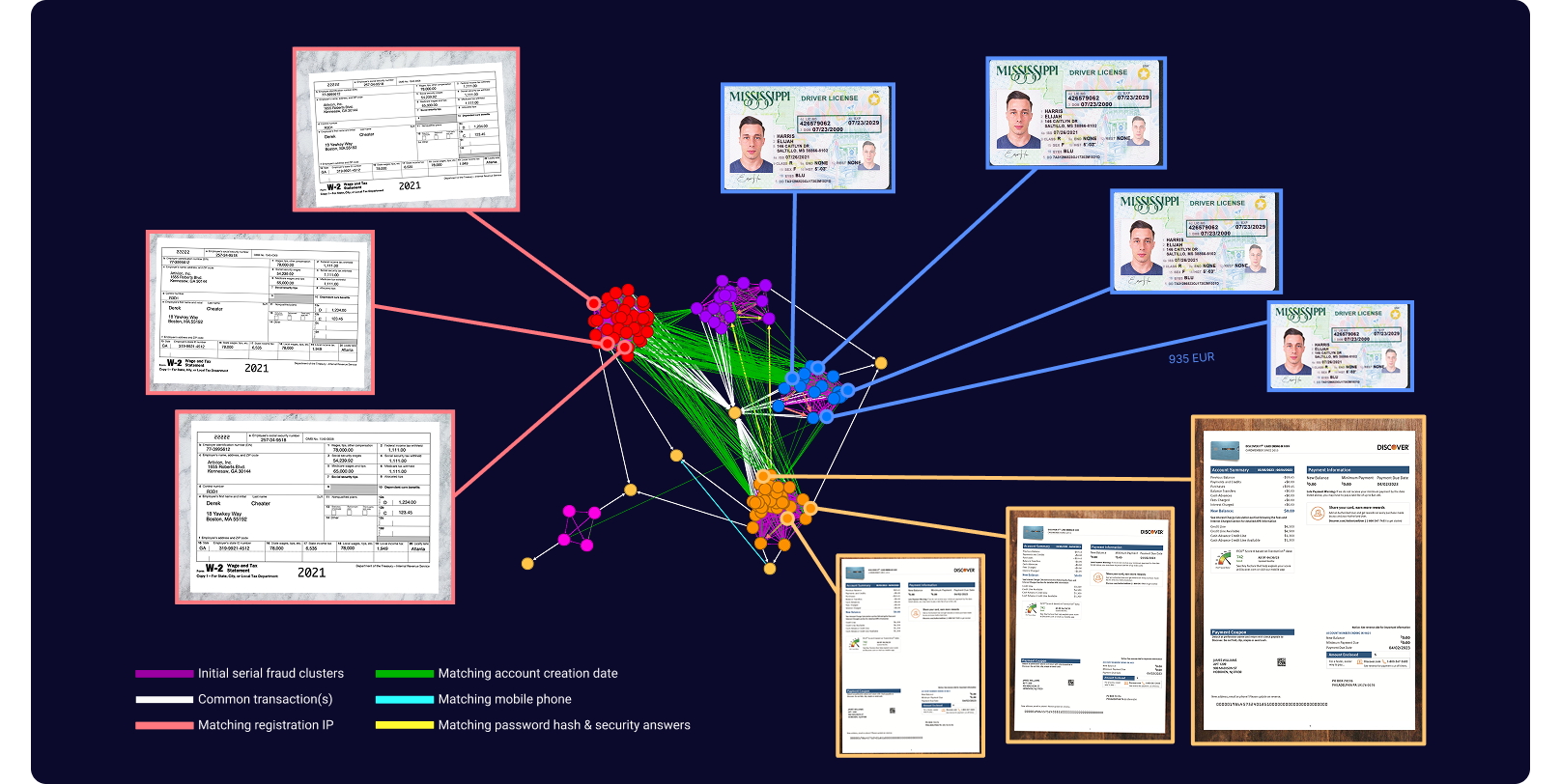
Find the patterns in passwords, security questions, phone numbers, company names, registration dates, and more...

Resistant AI has helped us to drastically reduce both the time it takes to catch fraud, and the amount of fraud that makes it past us to lenders.
- Ryan Edmeades MLRO and head of financial crime

Resistant AI has significantly helped prevent specific types of credit fraud, and enhances our ability to defend against document fraud attacks.
- Petr Volevecký Head of Credit Fraud Risk

Probably the best tool in our review flow. Resistant are our bionic eyes.
- Katarina Demchuk Identity Verification PM

Resistant AI perfectly complement FINOM's AML and Anti-Fraud program with its explainable AI, ensuring transparency to AML analysts as well as the regulator.
- Sergey Petrov Co-founder, COO

With Resistant AI, we can manage our known risks more efficiently while also identifying and adapting to previously unknown risks.
- Valentina Butera Head of AML & AFC Operations

Resistant AI prevents the manipulation of invoices submitted to our marketplace. It allows out investors to trade in security and saves my team a huge amount of manual work.
- Alexandra Belková Head of Operations
Go from layered defenses to a holistic risk-based approach
Layered defenses make life difficult for individual criminals. But to tackle the most advanced forms of fraud and financial crime, those layers need to talk and learn from each other. Turn weak signals into findings, and feed the right insight to the right team, at the right time.
High false positives, low recall, and endless spreadsheets of conflicting rules to update.
Catch more with less noise, without retraining your staff or ripping your existing TM systems.
Get unheard of fincrime prevention and productivity by feeding in Documents, behaviors, and other signals...






.png)